Demystifying Elastic SIEM
Introduction
Hey there! Following my recent presentation at the Elastic Community Event, I’m thrilled to extend the insights into setting up Elastic for cybersecurity tools. In this blog, we’ll take a hands-on approach, providing a detailed guide on leveraging Elasticsearch and its toolkit. Our focus? Building a robust Security Information and Event Management (SIEM) tool, seamlessly incorporating Suricata, Wazuh, Windows Sysmon, network packet capture, and Apache Webserver. All of this orchestrated within the dependable Proxmox stack and Debian server containers.
Unlocking Potential: Harnessing Elasticsearch
Let’s kick off with Elasticsearch, our foundation for this cybersecurity endeavor.
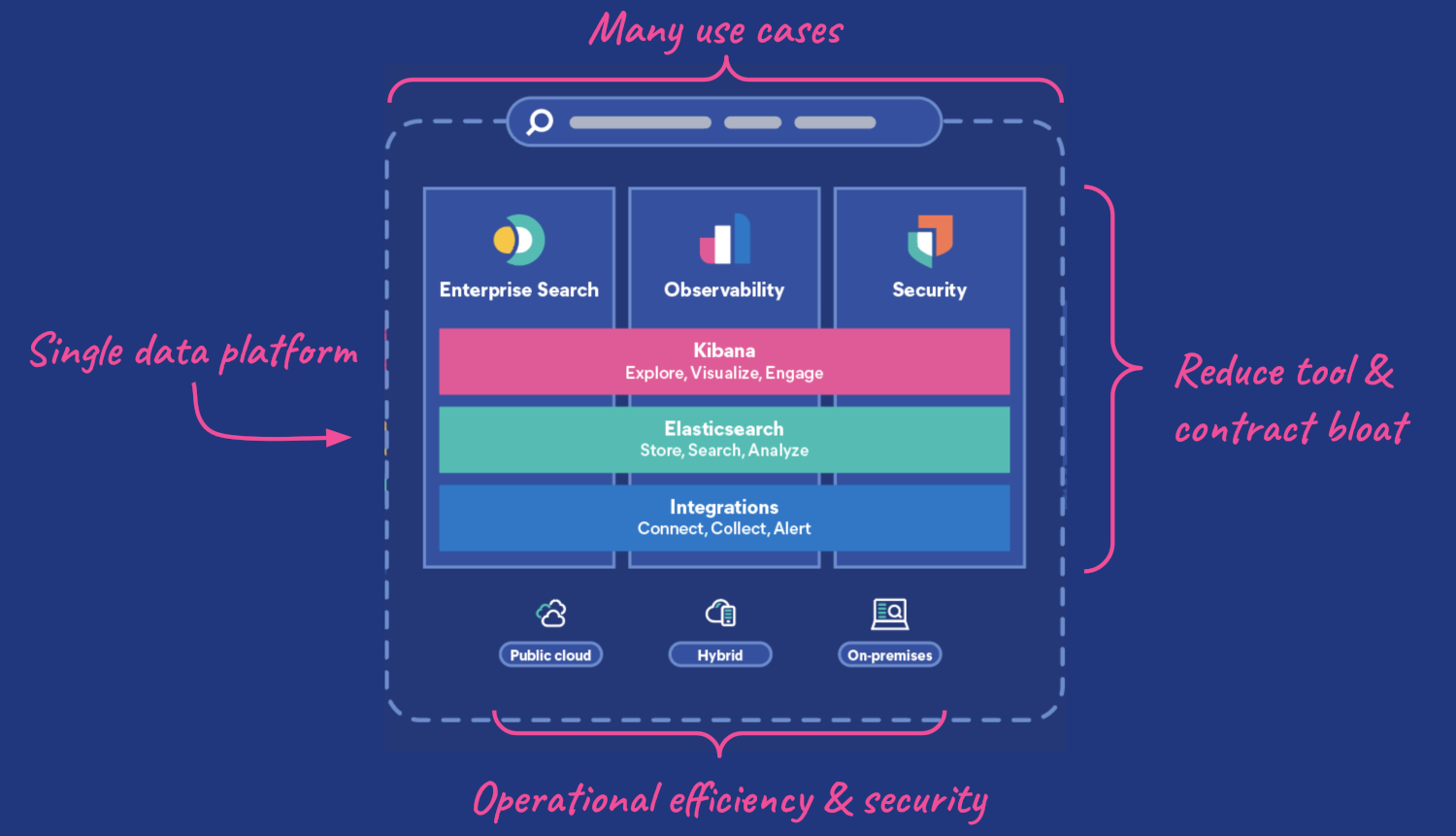
ElasticStack Use Cases
As an open-source, distributed search, and analytics engine, it offers scalability and real-time search capabilities. Think of it as the engine driving the aggregation, analysis, and visualization of diverse datasets.
SIEM stands for Security Information and Event Management It is a security solution that helps organizations detect, analyze, and respond to security threats. SIEM tools collect, aggregate, and analyze LARGE volumes of data from an organization’s apps, devices, servers, & users in real-time, so security teams can detect & block attacks.
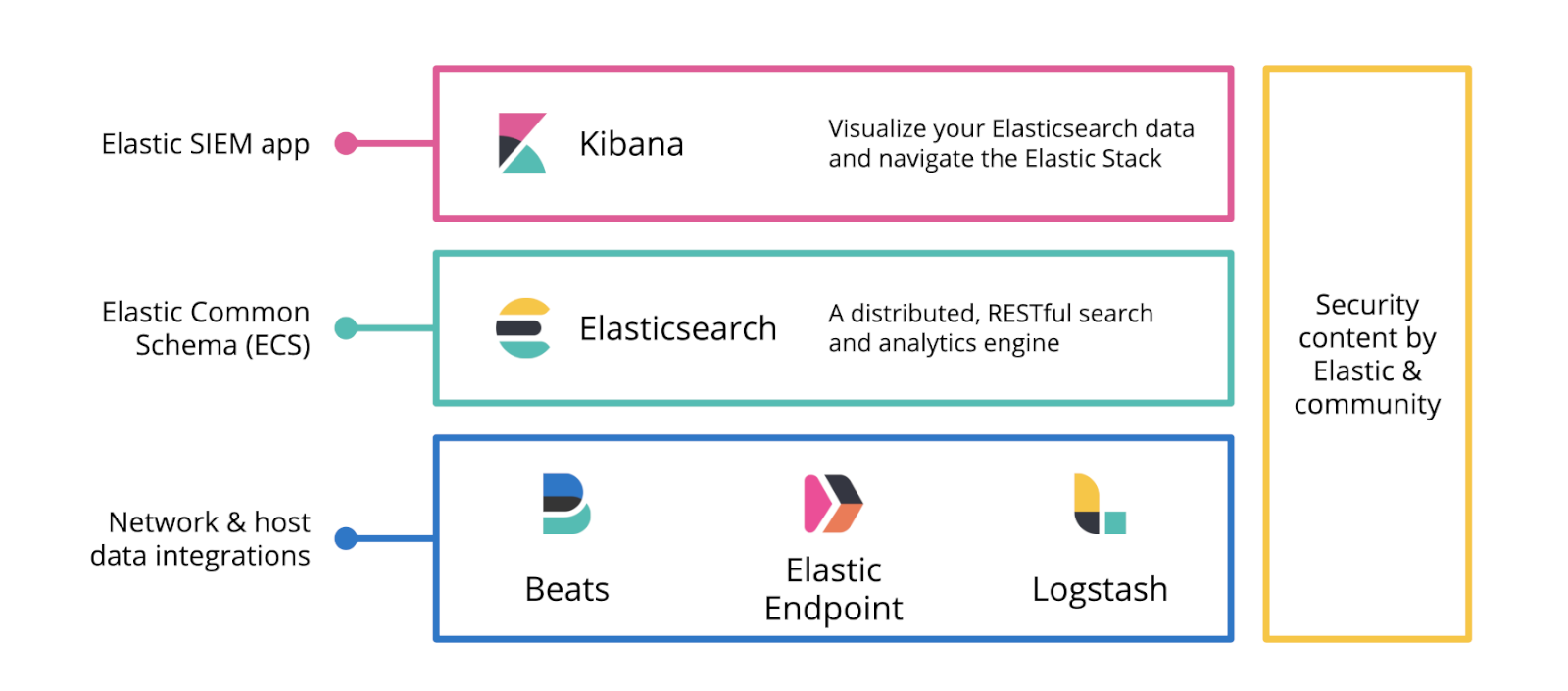
Overview of ElasticSIEM
Installing Elasticsearch and Kibana using Docker
Refer the Official and Latest Elasticsearch Installation Documentation and Kibana Documentation
On my personal setup, I created a docker container on a Proxmox LXC which you can download here
Tutorial: Adding an ElasticSearch Integration
We’ll learn to add an integration for an Apache2 Web Server Monitoring for a client machine using the Standalone Elastic Agent method.
Building the Arsenal: Integrating Essential Tools
Our SIEM’s strength lies in integration.
Suricata
Suricata isn’t just any security tool; it’s the sentinel that keeps a vigilant watch over your network. As a high-performance Network Intrusion Detection System (NIDS), Suricata boasts exceptional capabilities in identifying and thwarting potential threats traversing your network infrastructure.
Integration
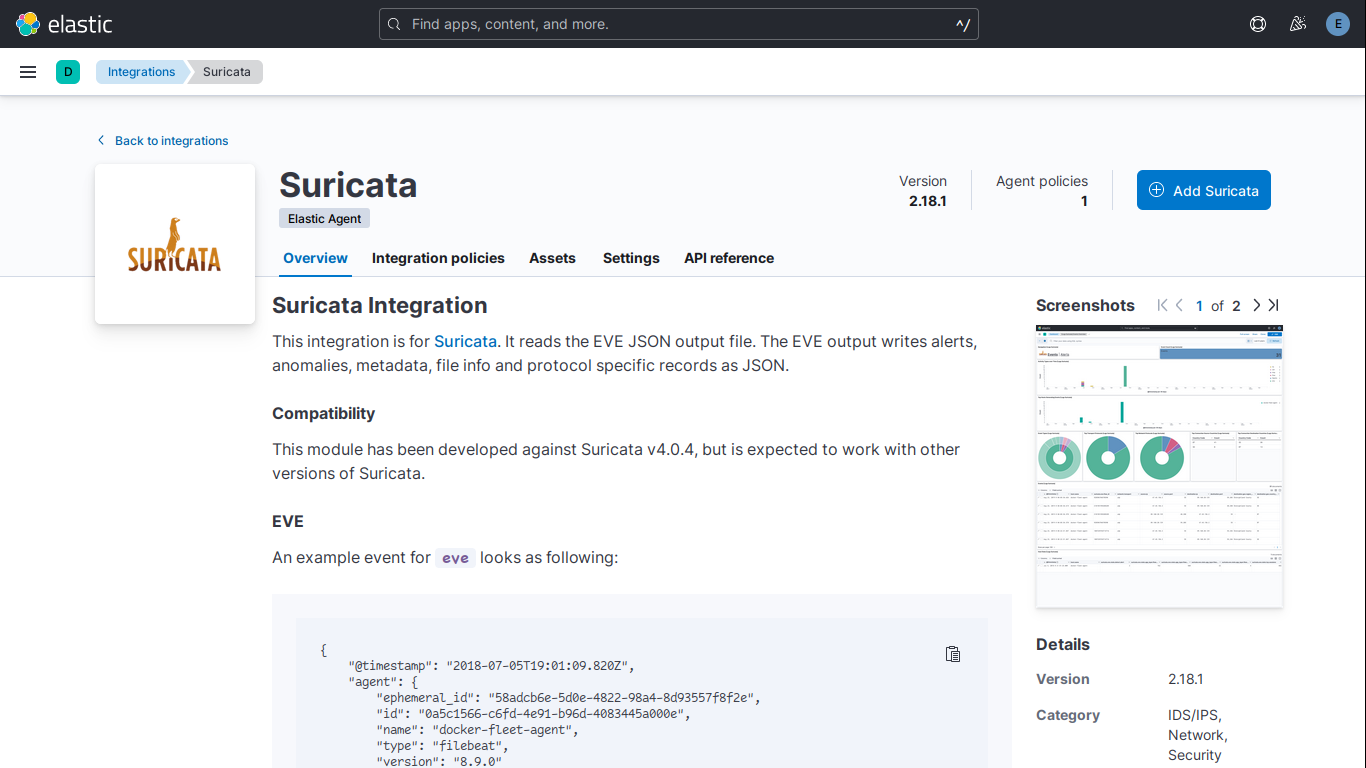
The integration of Suricata with Elasticsearch opens the doors to visualizing crucial security insights. Through the powerful visualization capabilities of Elastic SIEM, you gain a comprehensive view of Suricata’s detections and alerts, empowering you to respond swiftly to potential threats.
Dashboard

Real-Time Monitoring: The Suricata Dashboard serves as your real-time monitoring tool within the Elastic SIEM environment. It offers an intuitive interface presenting live data, alerts, and critical events detected by Suricata. This visual representation simplifies the process of identifying and responding to security incidents promptly.
Windows Sysmon
Windows Sysmon, short for System Monitor, is a powerful, lightweight system utility developed by Microsoft, designed to monitor and log system activity. It provides detailed information about processes, network connections, file changes, registry modifications, and more, aiding in the detection of malicious activity and troubleshooting system issues.
Integration

Sysmon operates by collecting event logs that record specific types of events related to process creation, network connections, file changes, and other activities on a Windows system. It can be configured to create detailed logs that contain information crucial for analyzing and investigating security incidents.
Dashboard

The Sysmon Dashboard within Elastic SIEM acts as your centralized hub for real-time monitoring and analysis of Windows system activities. This user-friendly dashboard presents a clear and comprehensive view of Sysmon-generated logs and events, allowing for swift identification and response to potential security incidents.
Decoding Conversations: Network Packet Capture
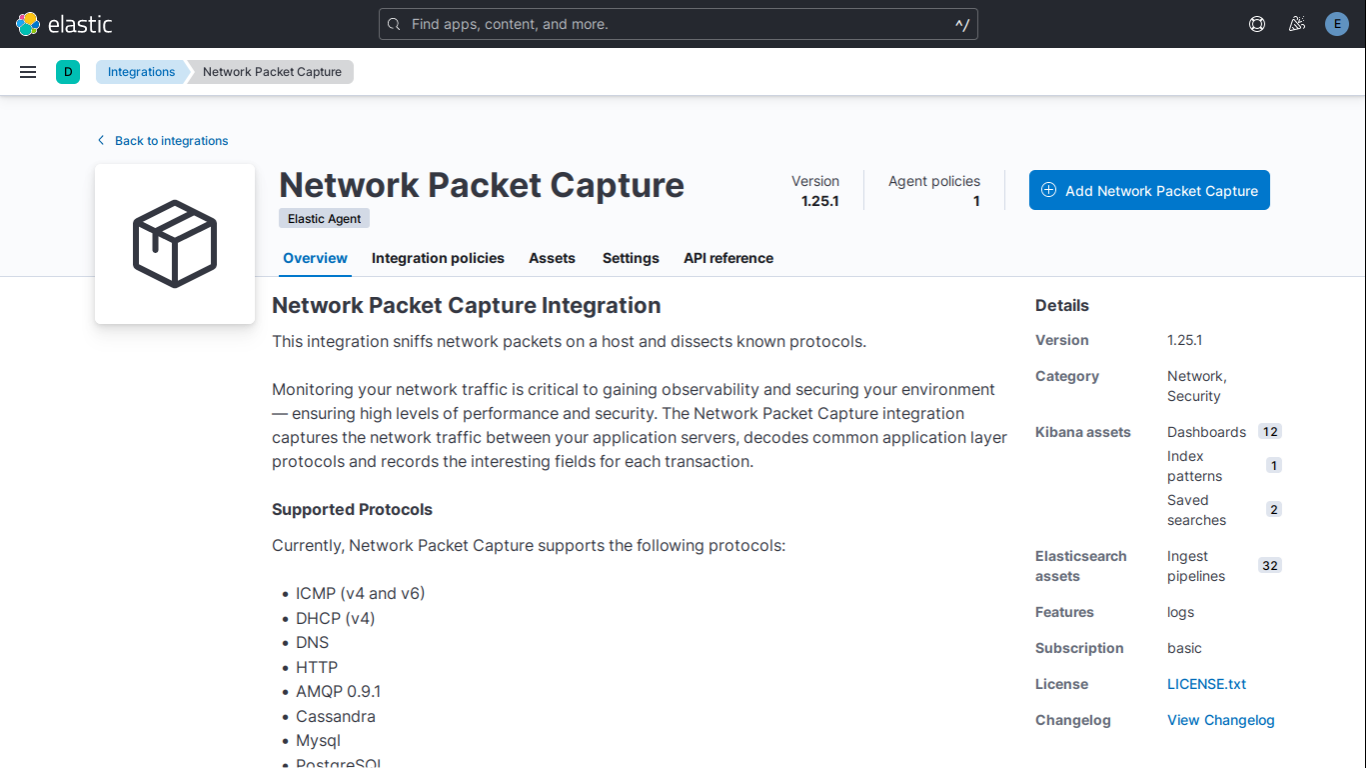
Network Packet Capture plays a pivotal role in cybersecurity by providing granular visibility into network traffic. Integrating Elasticsearch within the cybersecurity framework empowers analysts to effectively manage, analyze, and derive insights from this captured network data.

This integration not only enhances threat detection but also streamlines incident response and forensic investigations.
Securing the Web: Apache Webserver

Apache web servers generate extensive logs containing valuable information about incoming requests, user interactions, errors, and potential security incidents. Integrating Apache logs with Elasticsearch fortifies cybersecurity analytics by consolidating these logs into a centralized platform for efficient storage, indexing, and analysis.

The integration of Apache logs with Elasticsearch significantly enhances the capabilities of cybersecurity teams to detect, investigate, and respond to potential threats targeting web applications and server environments.
Architectural Symphony: Proxmox and Debian Synergy
In orchestrating this cybersecurity symphony, the Proxmox stack and Debian server containers take center stage. Their virtualization capabilities create a flexible and scalable environment, essential for adapting to the evolving cybersecurity landscape.

Conclusion: Empowering Cyber Defenses
Concluding this guide, we’ve navigated the intricacies of configuring Elastic SIEM, using Elasticsearch as the backbone and integrating various cybersecurity tools. This comprehensive approach, set within a Proxmox-Debian ecosystem, empowers cyber defenders to stay vigilant in the ever-evolving digital threat landscape. As we decode Elastic SIEM, the journey toward a more secure digital realm unfolds, offering cybersecurity enthusiasts the tools and insights needed for a resilient defense.
#elasticsearch #cybersecurity #siem-soc #blue-teaming #tools